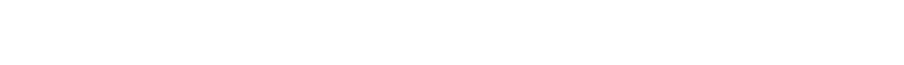A new security vulnerability has come to light, exposing over 6 million Chrome users to significant privacy and security risks. Research conducted by John Tuckner, a security analyst at Secure Annex, has uncovered 58 malicious Chrome extensions with the ability to secretly track user activities, steal sensitive data, and even execute remote commands. These extensions, which have been downloaded millions of times, often masquerade as harmless tools like coupon finders, ad-blockers, and privacy protectors.
The extensions were found to request overly broad permissions, granting them access to critical user information such as cookies, tokens, and browsing history. More alarmingly, these extensions are capable of monitoring user behavior, opening and closing tabs, and retrieving other private data—all while remaining hidden in plain sight.
A Growing Concern: Overly Broad Permissions
Chrome extensions are designed to enhance the functionality of the browser, but many of them request excessive permissions that go far beyond what’s necessary for their claimed functionality. According to recent research by the Cybernews team, a staggering 86% of popular Chrome extensions ask for highly invasive permissions, making users vulnerable to potential exploitation. The extensions uncovered in Tuckner’s research follow this dangerous trend, and most of them were found to contain hidden malicious code capable of inflicting serious damage.
Many of the 58 extensions were not listed on the Chrome Web Store and were instead unlisted, meaning they could not be discovered through normal search functions. They could only be installed through a direct URL, making them more susceptible to delivery via malvertising campaigns, phishing schemes, or fake update prompts. These methods allow attackers to target unsuspecting users with ease, especially those who are unaware of the potential risks posed by unlisted extensions.
Masquerading as Legitimate Tools
One of the most concerning aspects of these malicious extensions is how they disguise themselves as legitimate, trusted tools. Some claim to offer useful services such as coupon finding, ad blocking, or privacy protection, leading users to believe they are safe and trustworthy. In reality, they are embedded with covert functionality designed to spy on users’ browsing activities and steal valuable data.
Tuckner’s research uncovered extensions like Cuponomia – Coupon and Cashback (700,000 installs) and Fire Shield Extension Protection (300,000 installs), which claimed to protect users from other malicious extensions but, in fact, contained the very spyware they purported to defend against.
Key Indicators of Malicious Extensions
Tuckner’s research highlighted several red flags that suggest these extensions may not be what they claim to be:
-
Overly Broad Permissions: Extensions that ask for excessive access to browser data—such as cookies, tokens, and browsing history—are a significant indicator of potential malicious intent.
-
Misspelled Domains: Many of the malicious extensions communicated with misspelled domains, a common tactic used by attackers to obscure the true nature of their operations. For example, the domain unknow[.]com was identified as a major indicator.
-
Minimal Codebase: The extensions in question often featured minimal or even non-existent code related to their claimed functionality. Instead, the code was heavily obfuscated, making it difficult to analyze and raising suspicions of spyware or infostealer behavior.
-
Obfuscated Remote Control: The ability for these extensions to remotely control the browser and access sensitive data raised immediate concerns. These capabilities allowed attackers to monitor and manipulate browsing activity without the user’s knowledge.
The Danger of Featured Extensions
Adding to the concern is the fact that some of these malicious extensions were “Featured” on the Chrome Web Store, which could lead users to assume they were verified and safe. Tuckner expressed frustration with this process, questioning how extensions that are not discoverable via normal search functions can still be featured by Google. This inconsistency in the verification process further complicates users’ ability to assess the safety of their browser extensions.
What You Can Do to Protect Yourself
With over 6 million installations of these malicious extensions, it’s clear that this is not a small-scale issue. Google has been made aware of the findings, and some extensions have already been removed from the Chrome Web Store. However, not all of them have been taken down yet. To ensure your browsing security, here are some key precautions you can take:
-
Review Your Installed Extensions: Regularly audit the extensions installed on your browser. Remove any that you no longer use, or that seem suspicious.
-
Limit Extension Permissions: Be mindful of the permissions that each extension requests. If an extension asks for excessive access to your data (such as cookies or browsing history), it may be best to avoid it.
-
Check for Misspelled Domains: If an extension communicates with an odd or misspelled domain, it’s a red flag. Be cautious of extensions that rely on unusual domains for communication.
-
Avoid Installing Unlisted Extensions: Avoid installing extensions that cannot be found through the regular Chrome Web Store search feature. Only install extensions from trusted sources.
Conclusion: Stay Vigilant
The discovery of these malicious Chrome extensions serves as a stark reminder of the importance of cyber hygiene. As browser extensions become more powerful and prevalent, the risks associated with overly broad permissions and hidden functionalities also grow. By staying vigilant and following best practices, users can help protect themselves from these increasingly sophisticated threats.