January 2025 Update: Surge in Cyber Attacks Threatens Critical Network Devices
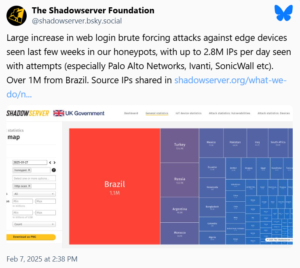
The Shadowserver Foundation has raised a critical alarm regarding an escalating cyber attack campaign, with over 2 million unique IP addresses targeting the web login panels of various network devices. This ongoing brute force login attack is affecting high-profile vendors, including Palo Alto Networks, Ivanti, and SonicWall, among others.
A Surge in Attack Activity: What’s Happening?
In recent weeks, attackers have been relentlessly bombarding honeypots—systems designed to lure cybercriminals with simulated vulnerabilities—with login attempts. These attempts suggest that vulnerable network devices, especially those with weak or unpatched login panels, are now prime targets for exploitation.
As of January 9th, 2025, Shadowserver reported a staggering 1.7 million participating IPs in the attack, a significant rise from the roughly 100,000 IPs observed in previous weeks. In total, the attack has involved over 2.8 million IP addresses per day, signaling the potential scale of the threat.
While HTTP-based scanning can sometimes be benign—such as when search engines index public content or security researchers scan for vulnerabilities—the sheer volume of this activity suggests a much more concerning scenario. Shadowserver believes this surge is part of a larger attack, likely originating from a botnet hunting for unprotected devices to compromise.
Targeted Devices and Vulnerabilities
The targets of these attacks are primarily network devices—routers, VPNs, and firewalls—which are frequently used in businesses and critical infrastructure. Recent vulnerability disclosures from major vendors have exacerbated the situation:
- SonicWall recently issued a warning about a critical flaw in its SMA 1000 series secure access gateways.
- Fortinet devices are facing active exploitation due to an authentication bypass vulnerability.
- Ivanti’s appliances have been targeted by suspected Chinese hackers exploiting two zero-day vulnerabilities.
- Palo Alto Networks firewalls remain vulnerable to exploitation, with hundreds of devices currently at risk.
These vulnerabilities have likely contributed to the rising wave of brute force attacks, with hackers targeting login panels to gain unauthorized access.
Origins and Scale of the Attack
The attack is largely originating from Brazil, which accounted for over 1.1 million IPs during the peak of the campaign. Other countries with high levels of participation include Turkey (135,000 IPs), Russia (133,000 IPs), Argentina (99,000 IPs), and several other regions around the world.
MikroTik, Huawei, and Cisco devices appear to be the primary targets of these attacks. However, in many cases, Shadowserver’s analysis was unable to directly link the source IP addresses to specific devices, which could suggest that compromised devices may be hiding behind other networks or proxies.
The Importance of Vigilance: How Can You Protect Your Network?
Network administrators are urged to remain vigilant as these attacks continue to evolve. Shadowserver is actively monitoring the situation and encourages administrators to investigate any suspicious activity or alerts they may receive, particularly if their networks are linked to the identified attack IP addresses.
Next Steps for Network Administrators:
- Review Your Device Configurations: Ensure that your network devices—especially those exposed to the internet—are using strong authentication methods and are running the latest security patches.
- Monitor for Unusual Activity: Regularly check logs for any signs of brute force login attempts or unexpected scanning activity.
- Engage with the Shadowserver Foundation: If you receive alerts about malicious activity from Shadowserver, it is crucial to investigate further and report your findings back to them for deeper analysis.
As cyber threats become more sophisticated, this incident serves as a stark reminder of the importance of securing network infrastructure and staying ahead of emerging vulnerabilities. The rise in brute force login attacks underscores the need for continuous vigilance and proactive defense mechanisms.
Stay secure, and ensure your systems are protected against evolving cyber threats.