Critical infrastructure has increasingly become a top target for cybercriminals. Over the weekend, we learned of the ransomware attack against a U.S. fuel company, Colonial Pipeline, that carries nearly half the fuel consumed along the U.S. East Coast. This is one of the largest disruptions of U.S. critical infrastructure by a cyberattack in history. It is a startling reminder at how vulnerable everything from our power grid to our water supply remains if we do not bolster our defenses.
“This attack will not be an isolated incident. We’ll continue to see destructive cyberattacks against industrial control system (ICS) environments, with energy, oil, gas and manufacturing companies as top targets for cybercrime cartels. These groups will leverage ransomware as a means of inflecting kinetic damage in the real world,” said Tom Kellermann, head of cybersecurity strategy at VMware.
On Monday, the FBI attributed the cyberattack to DarkSide, a group believed to be based in Eastern Europe. The VMware Threat Analysis Unit (TAU) analyzed DarkSide in February and found the group will customize the ransomware binary to the targeted enterprise. Similar to other variants of ransomware, it will utilize PowerShell to perform the deletion of volume shadow copies to ensure data cannot be restored easily.
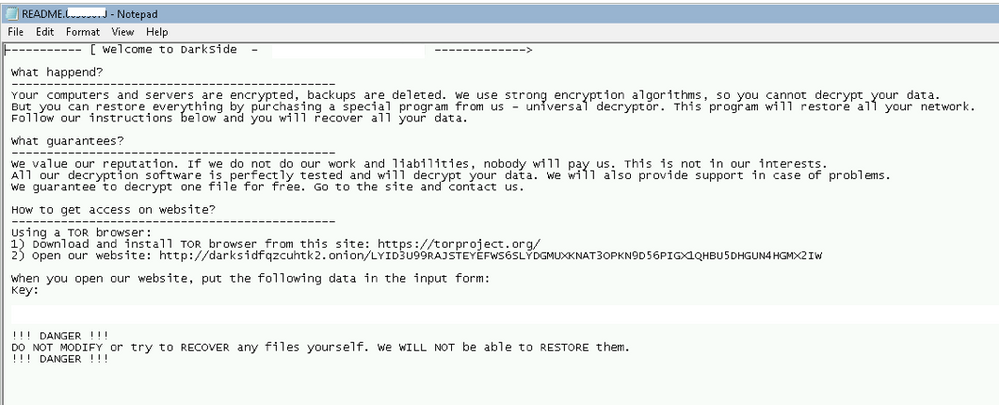
VMware TAU also identified DarkSide actively looking for affiliates to add to their operation via a dark web listing.
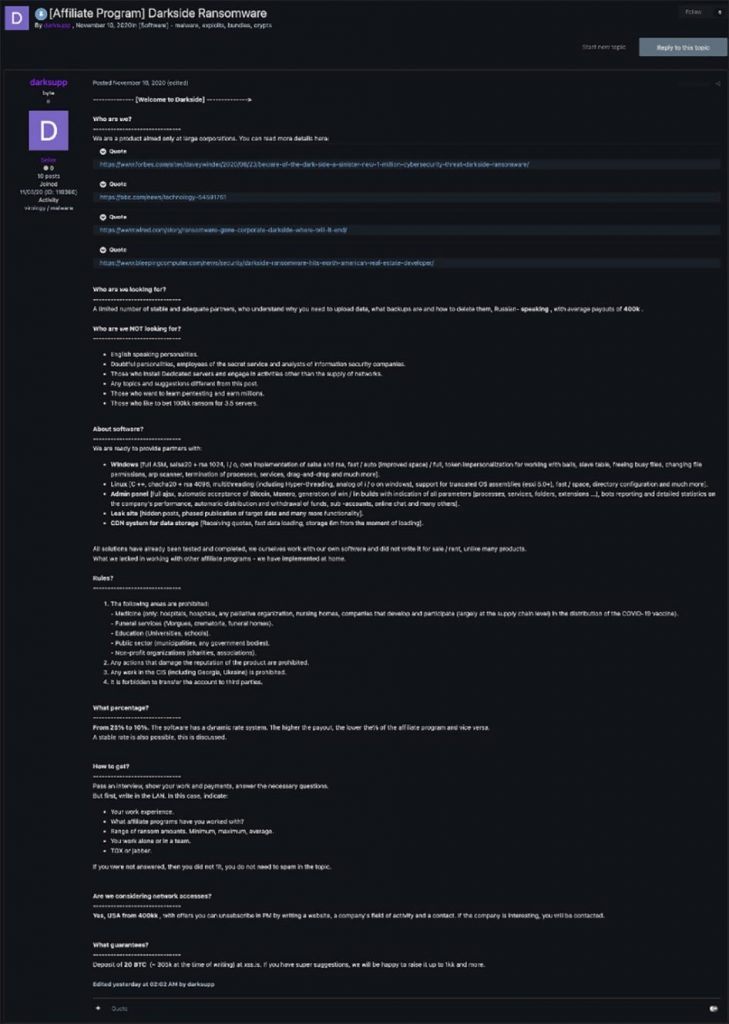
· Recent research from Digital Shadows provides an analysis of the DarkSide ransomware operation. While attribution is important, it is also necessary to understand the techniques, tactics, and procedures used during the pre-infection and post-infection phase of ransomware – focusing on the behaviors over the “who.”
The Rise in Secondary Extortion and RaaS
· Ransomware groups have widely adopted double extortion as a core tactic to ensure profitability. In fact, nearly 40% of security professionals said double-extortion ransomware was the most observed new ransomware attack technique in 2020.
· By taking time to quietly exfiltrate sensitive information from the organization, cybercriminals gain incrementally significant leverage on their victim organizations, forcing organizations to not only pay to decrypt their content but also prevent potentially harmful data from being sold or otherwise publicly disclosed. Thus, significantly increasing the impact and damage that ransomware groups can inflict upon their victims and sending a stark warning to others to protect their networks from this ever-evolving threat. To understand modern cybercrime, defenders must account for this as part of their security and resiliency programs.
· As ransomware-as-a-service (RaaS) explodes in popularity on the crimeware forums, cybercriminals are finding new and unique ways to deploy ransomware across organizations. Similar to how spies are recruited for espionage against government agencies, regular everyday people with access to high-value targets can be recruited to deploy malware. Often, they are lured through offers of significant sums of money or even a percentage of the ransomware payout, with some offering hundreds of thousands of dollars per victimized organization.
· Affiliate programs and partnerships between ransomware groups have also become a common occurrence alongside the general recruiting of insiders. These affiliate programs look to partner with initial access brokers – criminals that specialize in breaking into organizations and subsequently sell direct access and other ransomware gangs in order to improve their tradecraft, furthering their reach and overall profitability.
· As demonstrated by DarkSide’s post looking for affiliate partners, the global pandemic has empowered cybercriminals to work together capitalizing on the expanding attack surface. This attack only shows what security professionals have known for years: defenders must continue to work to stay one step ahead of attackers.
